Do you use WordPress to run your site or blog? You better head off to your dashboard to check for plugin updates. Now.
A cross site scripting vulnerability has been spotted in several WordPress plugins and themes, including popular ones like Jetpack, WordPress SEO, Google Analytics, All in one SEO, Gravity Forms, among others.
“The vulnerability Sucuri discovered would allow an attacker to send a WordPress user with administrative rights a link which could execute malicious JavaScript,” Jetpack said in a blog post announcing an update to its plugin.
Yoast has also released an update to its plugins, which are among the top used extensions in WordPress, to address the vulnerability.
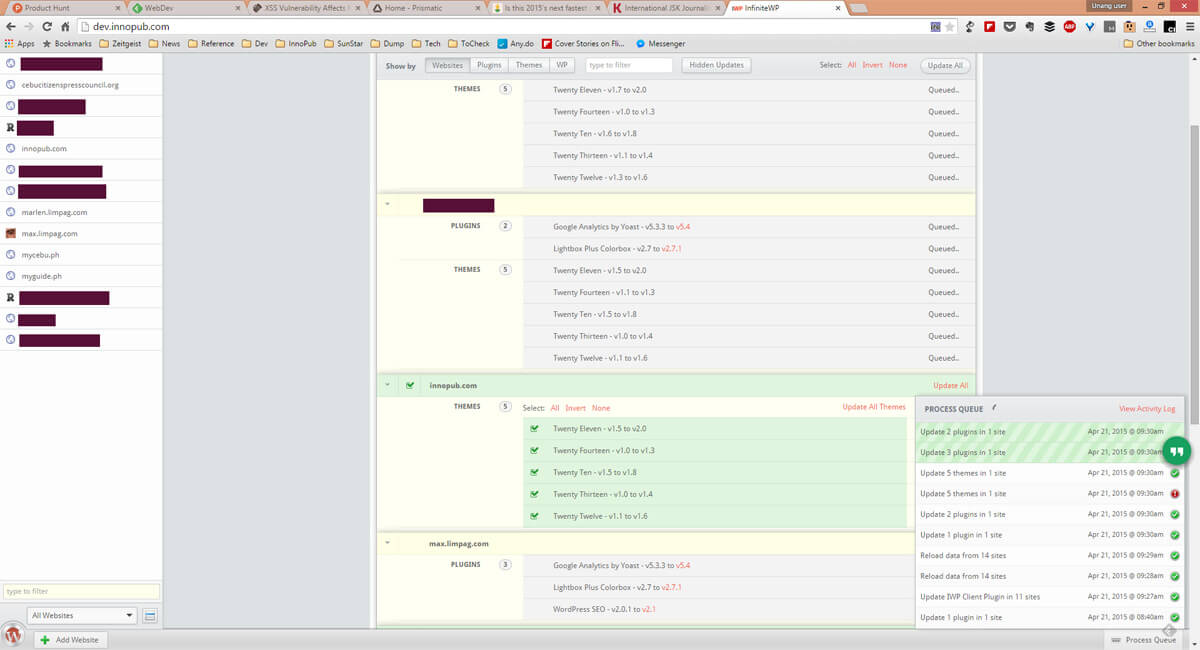
Why you should use InfiniteWP
It isn’t enough to perform available updates, WordPress admins need to monitor security announcements in the coming days because more plugins need to release new versions. Sucuri said they only scanned the top 300 to 400 plugins for the vulnerability.
If you run multiple WordPress websites, manually keeping up with and installing updates can be time-consuming and tedious.
You can, however, simplify the process by using a tool called InfiniteWP. It is a system that you install to centralize management of WordPress websites. From your InfiniteWP dashboard, you can upgrade the core WordPress, its plugins and themes of all your sites without having to log into each one of them.
InfiniteWP also allows you to back up the database and files of your WordPress sites.
I’ve been using InfiniteWP for some time now and it has saved me a lot of time in managing the WordPress installations that I run.
If you also manage multiple WordPress sites, there’s no question about it: you should use InfinteWP.
Max is a journalist and blogger based in Cebu. He has written and edited for such publications as The Freeman, The Independent Post, Today, Sun.Star Cebu, Cebu Daily News, Philstar Life, and Rappler.
He is also a mobile app and web developer and co-founded InnoPub Media with his wife Marlen.
Leave a Reply